Pragmatic Cybersecurity, Driven by People
Service Overview
In today’s rapidly evolving threat landscape, organisations face significant challenges in deploying, maintaining, and operating sophisticated security tools for threat detection, investigation, and response. Swarm-SecOps is a Managed SOC designed to alleviate these pressures.
Our SOC team is composed of cybersecurity specialists with a broad skill set and areas of deep expertise, organised to prevent, detect, analyse and contain cybersecurity incidents. We work in partnership with our customers to provide incident support and to build their response capability.
People
Our expert security analysts and engineers support your internal security team with specialised knowledge, advanced tools and proactive monitoring to keep your organisation secure.
Process
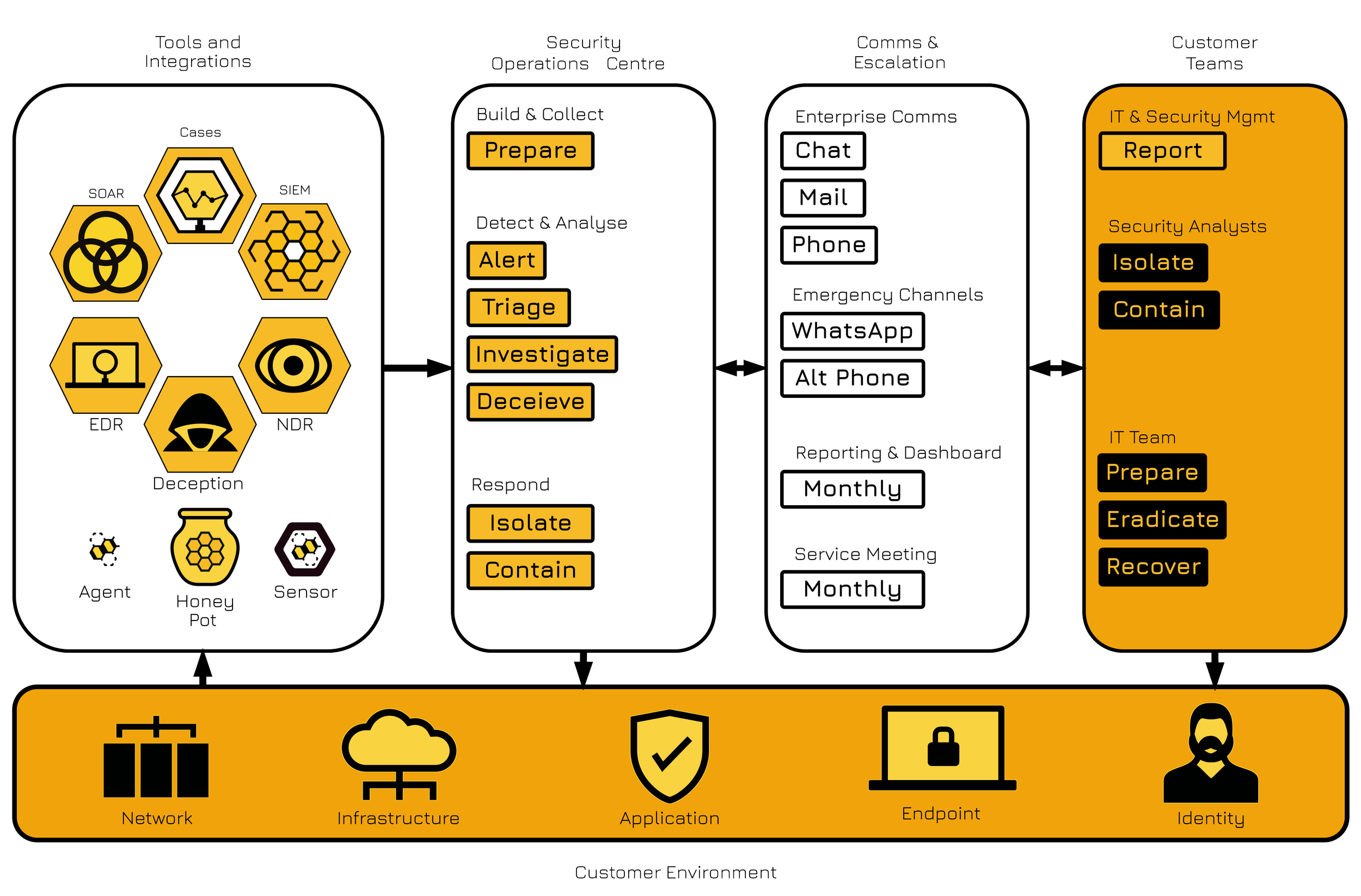
Swarm-SecOps services are organised into clearly defined tiers — Build & Collect, Detect & Analyse, and Respond — allowing us to tailor the level of engagement and seamlessly integrate with each customer’s existing IT & Security operations.
Technology
We deploy, manage and integrate industry-leading platforms — including SIEM, SOAR, endpoint, and network telemetry tools — to provide full visibility and rapid response. These technologies are managed by Swarm-SecOps and integrated into the customers infrastructure, ensuring flexibility and interoperability without disruption.
Co-Managed Security Service
Swarm-SecOps is built on a shared responsibility model that emphasises collaboration, transparency, and continuous improvement between our team and our customers.
As a co-managed SOC, we don’t simply deliver a alerts to your inbox — we work alongside your security and IT teams to build, monitor, and evolve your defences over time. Our engineers and analysts take ownership of the platforms, detection logic, and incident management processes, while our customers retain control of their business systems, access management, and operational environments.
This clear separation of duties ensures accountability while allowing both sides to operate efficiently within their areas of expertise. We maintain constant communication and shared visibility across tools, dashboards, and playbooks, ensuring that every decision — from alert triage to containment actions — is understood, agreed, and documented. Through regular service reviews, and continuous feedback, we grow the service together, adapting to evolving threats, infrastructure changes, and organisational priorities.
In essence, Swarm-SecOps is not a vendor-delivered service — it is a collaborative security partnership designed to evolve with you.
Service Value
Reduced Detection & Response Times
Automated enrichment and rapid analyst validation shorten the time it takes to identify, assess, and contain security threats.
Scalable Security Operations
Expand capabilities as your organisation grows, no need to rebuild platforms or retrain teams.
Expert extension of Your Team
Our specialised team integrates with yours, providing the expertise and focus needed to defend against today’s sophisticated threats.
Stronger Incident Containment
Pre-approved, orchestrated playbooks enable rapid isolation of compromised accounts, hosts, and network segments.
Reliable 24/7 Coverage
Always-on monitoring ensures threats are detected and escalated even when your internal teams are offline.
Reduced Operational Burden
We handle the heavy lifting of monitoring, triage, and investigation so your team can focus on core business priorities.
Automation First
Swarm-SecOps uses an automation first approach to handle repetitive, high volume tasks at machine speed, allowing analysts to focus on strategic investigation. Our SOAR platform automatically enriches, correlates, and triages alerts from EDR, NDR, SIEM, identity, and deception technologies to deliver faster, higher fidelity outcomes.
AI Enabled SOC
We use Generative AI carefully and with precision, supporting analysts by summarising investigations, generating case descriptions, and identifying meaningful patterns. AI assists decision making but never acts independently on customer environments, ensuring accuracy, control, and trust.
Our Approach
Build & Collect
Laying the foundation for effective security operations begins with robust infrastructure and meaningful data. The Build & Collect tier focuses on establishing the systems, integrations, and data pipelines needed to power detection and response. This includes System & Platform Build, Log Management and Threat Intelligence Curation.
Detect & Analyse
The Detect & Analyse tier focuses on turning collected telemetry into actionable intelligence through a balance of automation, enrichment, and analyst review. This automation layer aggregates and enriches alerts with contextual data — such as user, host, and threat intelligence information. Once triaged, each case is validated by a human analyst to ensure accuracy and situational awareness before any escalation or response action is taken.
Respond
Swarm-SecOps provides orchestrated response capabilities that allow for rapid containment of verified threats through pre-approved customer actions, while ensuring visibility, communication, and guidance throughout the incident lifecycle. We assist customers through the eradication and recovery process, providing technical expertise and coordination support
Swarm-SecOps Technology
The Swarm-SecOps technology platform is designed to provide comprehensive threat discovery and response across five key domains — Network, Infrastructure, Application, Endpoint, and Identity.
Our stack combines protective and detective technologies to monitor, correlate, and respond to malicious activity across the customer environment. Each technology plays a specific role within the overall detection fabric, while tight integration between systems ensures consistent visibility and a coordinated response.
Together, the NDR, EDR, Deception, SIEM, SOAR, and Incident Management components create a unified detection and response ecosystem. Protective technologies defend the perimeter and endpoints; detective tools provide deep visibility; orchestration ties them together for faster detection, verified accuracy, and orchestrated containment — all powered by people who understand your environment.